RANSOMCARE
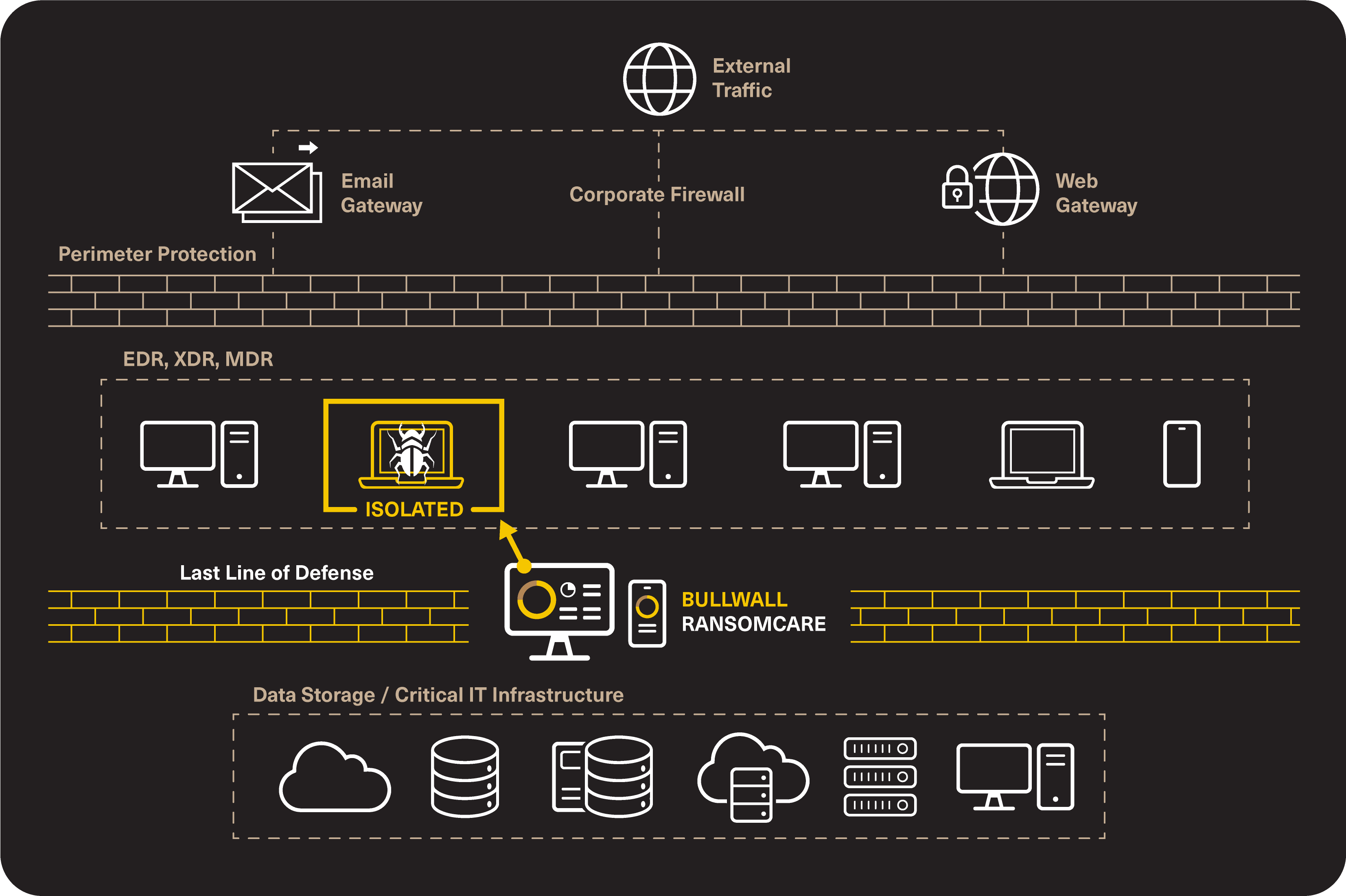
New strains of ransomware can disable endpoint protection, AV, firewalls, and even backup solutions before data encryption or exfiltration start. What do you do if your perimeter and endpoint protection is breached?
Our focus is to protect your data stores, not your endpoints.

RansomCare is the ransomware
containment layer you need
It detects and responds the very second
illegitimate encryption begins.
Here’s how it works...
Utilizes an Innovative Approach
RansomCare leverages heuristic analysis and file metadata to monitor traffic between endpoints, file shares and servers, both on-prem and in the cloud, to swiftly and efficiently detect evidence of an active ransomware breach.
Detects Known and Unknown Variants
Cybercriminals constantly monitor prevention-based security solutions for software updates. They know when existing variants are at risk of being detected and when to change their methods. RansomCare circumvents this problem entirely. Instead of searching for ransomware, RansomCare detects and responds to the behaviors indicative of ransomware: illegitimate file encryption and data exfiltration.
Employs a Lightweight Agentless Solution
RansomCare is not installed on endpoints or any existing file servers. Our agentless solution is easily deployed within days on a virtual machine, and leverages Machine Learning to configure itself automatically. RansomCare requires only read access to data and creates no network performance overhead.
Monitors all Your Critical Infrastructure
RansomCare works seamlessly with on-prem and cloud-based repositories such as Office 365, Sharepoint and Google Drive. Our solution is OS-agnostic to the device type accessing the cloud, including mobile devices, tablets, MAC, IoT, and laptops. It is also compatible with OS independent environments, such as Windows, Android, IOS and Linux. Comprehensive monitoring and protection for physical infrastructure components, including data servers, virtual machines, application databases, and domain controllers.
Covers all Entry Points
While most ransomware enters an organization through a phishing email, infections can also originate from a remote attack on a server, misconfigured cloud instances, remote desktop protocol, 3rd party contractors, or even USB and other removable media devices. Regardless of entry point, RansomCare reacts immediately when indicators of compromise are evident. RansomCare responds by isolating and containing the compromised device and user, instantly halting the active attack.
Seamlessly Integrates With Your
Other Security Tools
RansomCare integrates with all major SIEM and NAC solutions through JSON or a full featured REST API and pre-configured scripts. Most integrations are complete in under an hour. These integrations allow RansomCare to send full breach details to your platform of choice to alert your Security Operations Center (SOC) or response team, and initiate workflows as configured.
BullWall integrates with
the world’s leading security solutions

Today’s ransomware is capable of encrypting up to
25,000 files per minute per infected machine.
Only BullWall can stop it

